seminar topics:
submitted by:M.Rafahnah Yasmeen II-MCA
MESSAGE CONFIDENTIALITY AND MESSAGE AUTHENTICATION
Confidentiality, integrity and availability, also known as the CIA triad, is a model designed to guide policies for information security within an organization. The model is also sometimes referred to as the AIC triad (availability, integrity and confidentiality) to avoid confusion with the Central Intelligence Agency. The elements of the triad are considered the three most crucial components of security.
In this context, confidentiality is a set of rules that limits access to information, integrity is the assurance that the information is trustworthy and accurate, and availability is a guarantee of reliable access to the information by authorized people.
Confidentiality:
Confidentiality is roughly equivalent to privacy. Measures undertaken to ensure confidentiality are designed to prevent sensitive information from reaching the wrong people, while making sure that the right people can in fact get it: Access must be restricted to those authorized to view the data in question. It is common, as well, for data to be categorized according to the amount and type of damage that could be done should it fall into unintended hands. More or less stringent measures can then be implemented according to those categories.
Sometimes safeguarding data confidentiality may involve special training for those privy to such documents. Such training would typically include security risks that could threaten this information. Training can help familiarize authorized people with risk factors and how to guard against them. Further aspects of training can include strong passwords and password-related best practices and information about social engineering methods, to prevent them from bending data-handling rules with good intentions and potentially disastrous results.
A good example of methods used to ensure confidentiality is an account number or routing number when banking online. Data encryption is a common method of ensuring confidentiality. User IDs and passwords constitute a standard procedure; two-factor authentication is becoming the norm. Other options include bio metric verification and security tokens, key fobs or soft tokens. In addition, users can take precautions to minimize the number of places where the information appears and the number of times it is actually transmitted to complete a required transaction. Extra measures might be taken in the case of extremely sensitive documents, precautions such as storing only on air gaped computers, disconnected storage devices or, for highly sensitive information, in hard copy form only.
CONFIDENTIALITY WITH SYMMETRIC CRYPTOGRAPHY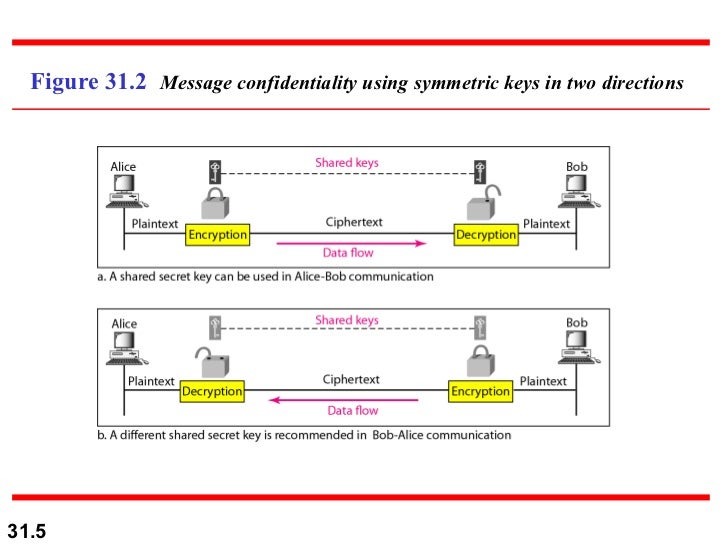

- modern Symmetric key are more complex.
- sender and receiver shares a secret key.
- use symmetric key cryptography,find solution to the key sharing.this is done by session key.
- session key used only duration of one session.
- using two different keys more secure one.
- one key is compromised.another is confidentiality.
- for a long message symmetric key more efficient than asymmetric key.
CONFIDENTIALITY WITH ASYMMETRIC CRYPTOGRAPHY
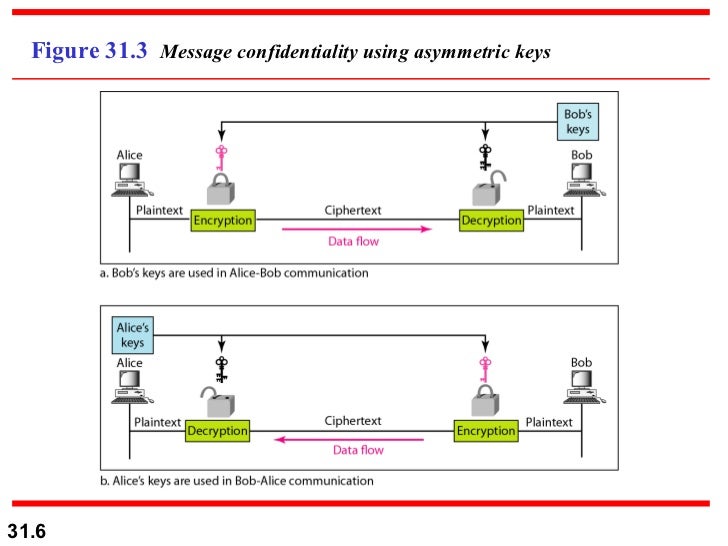
- there is no key sharing.
- it has a public announcement.
- bob creates two keys.one private is receiver,another public is sender.
- public key lock the message.private key unlock the message.
- two pairs of keys used.
- alice sends a message to bob,she use a bob pairs.
- bob sends a message to alice,he use a alice pairs.
- it has applied only short messages.
MESSAGE AUTHENTICATION
In cryptography, a message authentication code (MAC), sometimes known as a tag, is a short piece of information used to authenticate a message—in other words, to confirm that the message came from the stated sender (its authenticity) and has not been changed.
- a hash function does not authenticate sender side.
- to provide message authentication, alice need to give a proof .
- this hash function is normally called message detection code.
- this code detect any modification of a message.
MESSAGE AUTHENTICATION CODE(MAC)
- message authenticate ,need to change MDC to MAC.
- MDC is a keyless function.
- MAC is a keyed function.
- MAC was symmetric key between sender and receiver.

HASHED MESSAGE AUTHENTICATION CODE(HMAC)
- HMAC Creates a nested MAC by applying a keyless hash function to concantinate of a meassge and a symmetric key.

finally receiver receives the HMAC and message.HMAC is authenticate and validity of a origin of a message.